Managed Detection & Response
Hackers are Targeting Small Businesses. It’s Time to Fight Back.
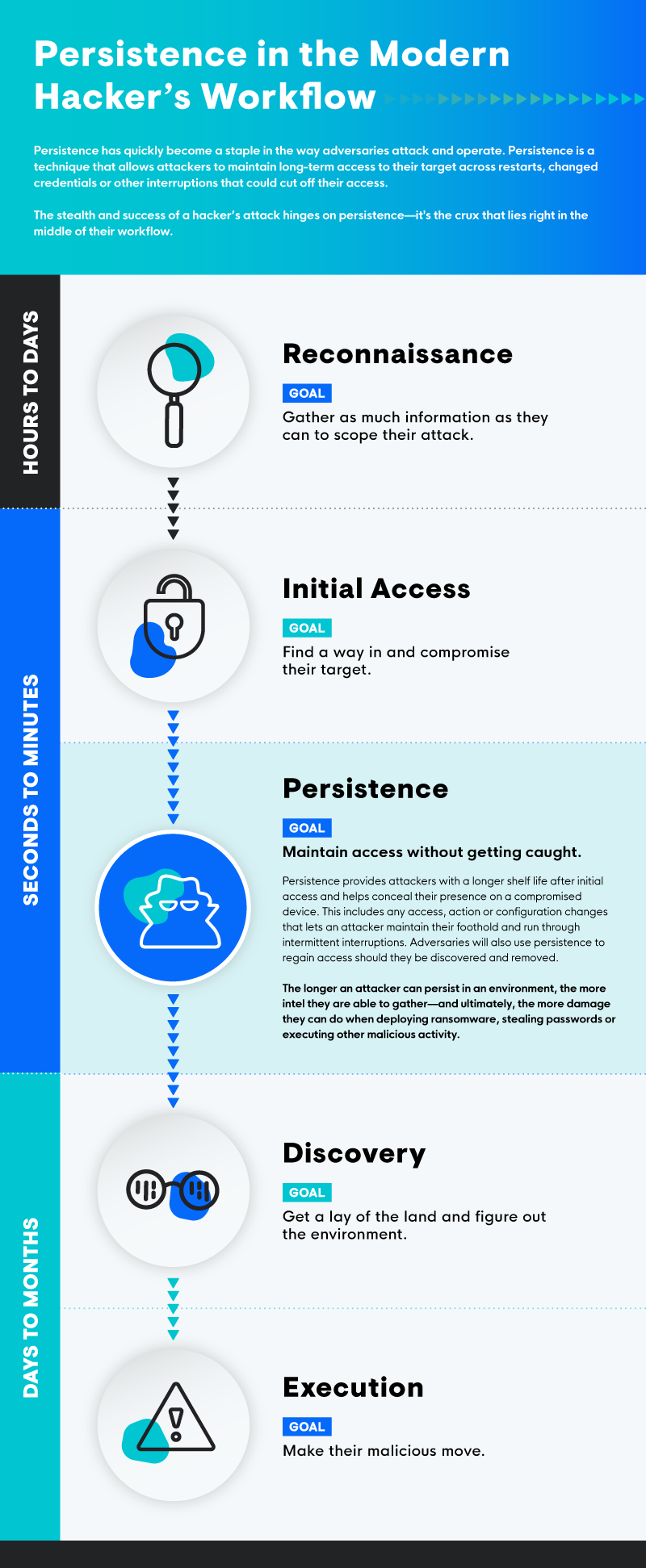
Who’s Hiding In Your Network?
Did you know that hackers spend an average of 24 days in a network before being discovered? The longer an attacker can persist, the more effective and damaging their eventual attack will be.
Small businesses can no longer fly under the radar of cybercriminals. In fact, they are being directly targeted because they’re less protected (and more vulnerable) than large enterprises.
So what happens when a hacker slips through the cracks undetected? How long will they spend undetected in your environment? What sensitive information will they capture and at what point will they deploy ransomware and fully encrypt your systems leaving your important files , emails and local backups useless?
Managed Detection & Response
To protect our clients from these ever evolving threats, we offer a Managed Detection and Response (MDR) solution as part of our security stack. This added layer of protection is designed specifically to look for these hidden threats, changes in device behavior and “quiet” indicators of compromise that other tools miss. These alerts are monitored by a 24/7 Security Operation Center. Each potential threat is reviewed by a human security expert and the system either locked down immediately, or for non-urgent issues a report is generated to follow up with you during regular office hours.
Think of it as a safety net or the backup cord on a parachute; if your primary defenses fail, MDR provides active threat hunting that can be the difference between a quick recovery – or a major incident.
Hackers have upgraded their systems. It’s time to upgrade yours.
Transform Defence Into Offence
Don’t let your business become another statistic.
With multiple layers of advanced software, smart policies and 24/7 security response, our cybersecurity solutions provide the peace-of-mind you need to focus on growing your business – not just protecting it.
Ready to talk features or take a look under the hood?
Fill out the form below to schedule a personalized consultation.
Interested in fully Managed IT Solutions? Check out or Managed Services Packages
Learn More
How Persistent Threat Hunting Works
Collect
Our software collects data from your desktops, laptops and servers. The data is sent to a cloud-based engine for automated review. This process is invisible to users.
Analyze
Once captured, our threat operations team manually reviews suspicious or potentially malicious activity to eliminate false potivies and identify real threats to your network.
Remediate
If an active threat is present, our team will isolate and remediate any effected machines. We’ll also coordinate directly with you if any additional steps are required to ensure the threat is properly handled.